In this paper, we show that the wallet can handle the whole authentication process mutually after it has been setup by the user once. We also improved the setup procedure by cryptographically embedding a web site-bounded random value into the account password. This value is unknown to the user. On the one hand, we prevent that the user applies low-entropy passwords to set up an account. On the other hand, we ensure that the user does not use the same password for different accounts.
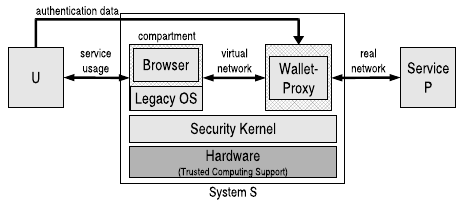
To realize a transparent usage and in order to provide a safe environment during the account setup, the wallet also works as a network proxy. Hence, the wallet must be capable to parse HTML web sites and to react accordingly, e.g., by initiating the setup procedure.
To protect the confidentiality of the user’s credentials, we use the sealing functionality of a Trusted Platform Module (TPM): We bind the secret data to the integrity measurements of the wallet and the underlying security kernel. This means, the credentials are encrypted using a key that never leaves the TPM, and the decryption is only possible if the same measurement values are logged into the TPM during the boot process as they were taken at encryption time.
More information [Technical Report] [Slides]

No comments:
Post a Comment